
University of Split
ABSTRACT: The number of acts of piracy at sea has dramatically increased in recent years. In the age of globalization, piracy is not a trivial phenomenon - it is a global organized crime which currently poses the largest human threat at seas and oceans. In this article, models of preventive and timely effective operations of the ship against possible pirate attacks have been systematically analyzed, as well as the actions of the defence ship against pirate attacks during the sailing in piracy areas and beyond. Based on the results, after carrying out the research, the model of prevention of possible pirate attacks against the ship was made, with developed Risk Assessment model, Game Theory model, and proposed improvements to protect the ship against pirate attacks by means of simulations of different attacks scenarios made by the use of Petri nets.
KEYWORDS: pirate attack, the ship protection, risk assessment, game theory, high risk area
Recent Research
In recent studies in both domestic and foreign scientific and professional literature, the authors mainly deal with the study of a particular segment of pirate attacks on ships and how to determine to avoid such attacks. Recently, research has been exploring the possibility of defence of the ship against pirate attacks, including a large number of significant influencing factors. The articles important for the research in this paper are as follows: Thomas Lucas and Thomas Tsilis (2011) in their article Counter-piracy Escort Operations in the Gulf of Aden. [19] In their research, the authors developed simulations of identifying key factors involved in the transit of ships through the Gulf of Aden, particularly those carrying sensitive cargo and equipment. There was a scenario made in which a group of merchant ships were sailing with the guidance of a warship escort. More than 300,000 simulations of Escort Missions were created. The results achieved show how to form the convoy, the number of ships in the convoy, the transit speed and the positioning of the warship in relation to the ships in the convoy, and the detection of potential pirates. The literature that has been analyzed mostly consists of papers that give only partial approach to the problem of protecting ships against pirate attacks.
Pirate Attacks On Ships And Their Defense [3]
The latest statistical data show that the total average number of pirate attacks in the world is in decline, and this average decline is contributed by the decline of pirate attacks in the Gulf of Aden. However, in the areas of Indonesia and Malaysia, the west coast of Africa (Nigeria, Guinea), the number of attacks is still increasing. In the area of Indonesia and Malaysia due to very large, indented coastline and large sea area which requires monitoring, it is very difficult to establish a permanent presence of military forces within the whole area. This clearly indicates that the pirates quickly adapt to new circumstances and changing tactics. They use increasingly sophisticated, aggressive, brutal and inhumane methods both during their attempts to capture ships and after the capture. Their activities are focused on the areas of open sea (Indian Ocean) and wide areas of Indonesia and Malaysia with a large number of islands where there is no permanent presence of military forces.
In addition to the physical barriers that are set up on board to make access to ship decks more difficult, the practice of engaging the Private Unarmed Security Teams (PUST) and the Private Armed Security Teams (PAST) has been established for the protection of ships, all with the consent of the international community, insurance companies, shipping companies and the flag state of the ship. Also, a large engagement of modern technology has been recorded.
The Mediterranean Sea is one of the busiest waters in the world and, according to UN data, as much as 15% of the world's total maritime traffic sails in that sea, therefore, such a “black scenario” could have serious consequences globally [12]. Vessels with ISIL immigrants could be used in suicide missions. The Italian Ministry of Defence prepared a detailed analysis of how the ISIL could gain control over the Mediterranean Sea. In taking control over some ports and vessels they can take advantage of the experience of traders that have been involved in human trafficking along these routes for years. This analysis shows that they would be able to use speedboats to attack the fishing and commercial vessels, port terminals, offshore installations, and to use vessels with immigrants in suicide missions.
Factors For Successful Piracy Attacs And Their Features [3]
In order to obtain insight into the condition of the ship, assess its reliability, and on the basis of that make a ship risk assessment, it is necessary to determine the factors that will be monitored and analyzed. The classification of the factors is partially taken from the results of Thomas Lucas and Thomas Tsilis (2011) [19] and Hans Liwang Chalmers, Jonas W. Ringsberg Chalmers and Martina Norsella (2013) [7], as these classifications are considered to be appropriate and well done. Based on their research results, the factors are classified as:
- Decision Factors - DF,
- Noise Factors - NF,
- Criteria for better convoy protection.
Decision Factors (DF) are factors that we can influence, or they can be controlled in real environment, such as: the position of a military ship in respect to merchant ships in the convoy, the speed of the convoy, the number of merchant ships in the convoy, the distances between merchant ships, the delay in the take-off of the helicopter, private unarmed maritime security, private armed maritime security, construction characteristics of the ship according to the type and size of the ship, setting of physical obstacles.
Noise Factors (NF) or uncontrolled factors are those factors that cannot easily be controlled in the real environment and / or, it could be done only at high cost, such as: the number of pirates that can attack the ship / convoy, the response / waiting time in communication between a merchant ship under attack and the military ship, the speed of a pirate ship, the pirate distance from the merchant ships / ship that discovered the pirate's identity and their speed increase at a time when they were identified as pirates, wind force, sea state – wave height.
The most influential factors in the ability of defence against pirates are the number and speed of pirate ships, speed and/or convoys in transit, the height of the freeboard and PAST. The obtained results show that the better protection of convoys and lesser vulnerability of merchant ship in the convoy are achieved if the following criteria are met: formed convoys, convoy transit speed, position of the warship in front or at the sides of the convoy, position of the warship behind the convoy, simultaneous attack of pirates with fewer than three pirate ship, simultaneous attack of three or more pirate ships.
As for the use of armed escorts on ships, it significantly increases the chances of defence against kidnapping attempts. However, it can also increase the risk for the crew and additional security staff, if the pirates take a ship during the exchange of fire. Therefore, the use of armed escorts should be carefully considered and should be avoided unless there is another appropriate means of protection of the crew, ship and cargo. There are also legal problems that are attributed to the use of PAST [18]. Unarmed and armed guards have their advantages and disadvantages. Therefore, it is always necessary that shipowners carry out thorough check and risk assessment before recruiting PAST staff. The risk assessment should include factors such as the routing, ship design, type and purpose of the ship, the freeboard height, speed, planned operation. As the PAST measures proved to be very effective, there is a danger that governments may try to institutionalize the armed protection of the ship and thereby shift the responsibility for maritime security from the coastal state to the shipowners.
Techniques of Ship’s Protection Against Pirate Attacks [3]
Speed is one of the most effective ways of rejecting a pirate attack. By increasing speed it is possible to try to escape the attacker and/or make it difficult for him to embark the ship. From the available statistical data of the International Maritime Bureau (IMB) and the Office of Naval Intelligence (ONI), it is obvious that the pirates continue to successfully attack the ships that sail at a speed of 14 knots or less. However, they also demonstrated the ability to board ships of 18 knots, but only when the weather conditions and the state of the sea were extremely favorable. There have been no reported pirate attacks on a ship with a freeboard exceeding 8 meters sailing at a speed of over 18 knots. However, it is possible that the pirates develop new tactics and techniques that would allow them to get on the ship that is moving fast. [1], [7]. Therefore, additional protective measures should always be taken into account. It is very likely that pirates will try to attack at the most vulnerable points of the ship, and that is:
- Command Bridge, which they attack firing at the Bridge with light firearms or heavy weapons such as hand-held missile launchers, and
- the lowest point of the ship above the water line, making it easier to climb the ship. These points are often on both quarters of the ship, immediately in front of, and on the port and starboard sides of the stern superstructure located on the stern of the ship.
Proper and skilful ship manoeuvring can make it very difficult and/or disable a pirate to access the ship. Performing the ZIG-ZAG manoeuvre helps create positive pressure on the bow and stern. Keeping the skiff in the stern or bow positive pressure zone makes it difficult, or disables the access because the pressure permanently pushes the pirate away from the ship (the blue marked area).

Fig. 1, ZIG-ZAG manoeuvre - creating positive pressure on bow and stern (rejection area),negative pressure in the centre of the ship in navigation (intake/attraction area). Source: Made on the ship simulator TRANSAS NTPro5000
However, if the skiff approaches the ship in the amidships area, where the negative pressure is present, the skiff zone will be sucked in, or drawn to the middle zone of the ship (the red marked area). That is why such situations should be avoided and in any case disallowed.
Pirates plan to test the feasibility of the approach and the embarkation and try to intimidate the ship by slowing it down or stopping it to allow easier boarding. Therefore, special attention should be paid to the ballistic protection (protection against bullets, grenades and various debris as a result of an explosion) of the crew that needs to remain on the Bridge during pirate attacks, knowing that pirates have carried out an open fire on the Bridge trying to force the ship to stop [28].

Fig. 2. Physical barriers to protect certain parts of the ship. Source: Private archive
To enable the ship to pass through areas of possible pirate attacks successfully, with no significant adverse effects from pirates, the most important are structural features and speed of the ship. The structural characteristics refer to the design of the ship’s stern and bow and the height of its freeboard.
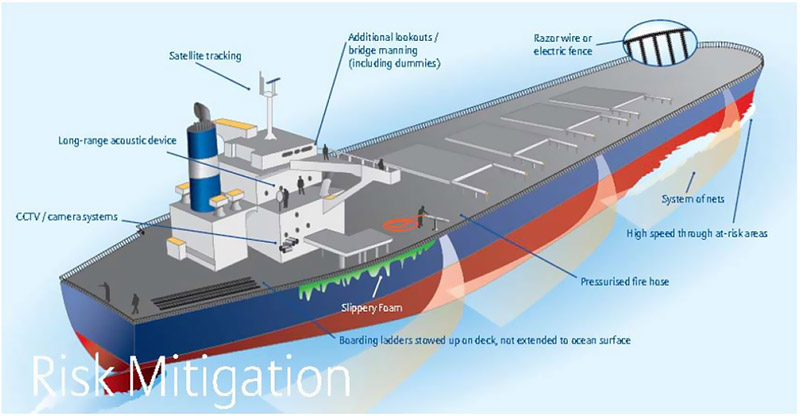
Fig. 3- BMP types of physical protection measures against pirates. Source: Allianz - Piracy: An ancient risk with modern faces, an insurer’s perspective from Allianz Global Corporate & Specialty)
In many cases merchant ships managed to defend themselves against pirate attacks using passive measures such as increased defence observations, night transit through the high risk area, the use of fire-fighting nozzles, steam, foam, increase of speed and performance of proper controlling manoeuvres by ship.
Time Dynamics of Pirate Attacks [3]
In the simulation of the dynamics of events during the pirate attack as the most appropriate tool, Hybrid Time Petri Nets [4], [11], [20] were selected. By their use the most unfavourable cases of pirate attacks on a ship at sea were developed, presented and analyzed, with additional protection of the warship with a helicopter with the following pirate strategy (I):
- Pirate Strategy (I1) – a pirate attack scenario with one pirate ship,
- Pirate Strategy (I2) – a pirate attack scenario with two pirate ships,
- Pirate Strategy (I3) – a pirate attack scenario with three pirate ships.
Such a system in its nature is very complex. It consists of the Continuous Systems, i.e. the motions of the attacked ship, the movement of a pirate ship and the movement of a military ship/helicopter (change of speed, distance), and discrete event systems, i.e. the beginning of a Discrete Event Systems, i.e. the beginning of an attack, sending distress.
Pirate Strategy (I1) – A Pirate Attack with One Pirate Ship [3]
The Petri Net in Figure shows an attack with a pirate ship accompanied by a warship (helicopter):
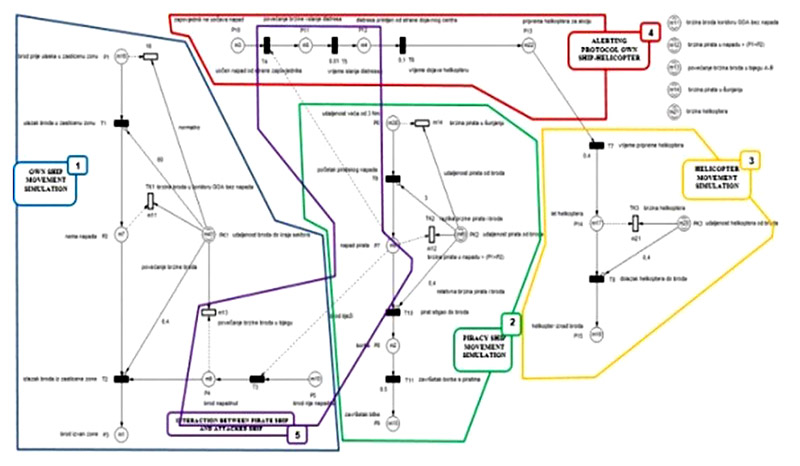
Fig. 4. Attack with a pirate ship accompanied by a warship (helicopter) – explanation of individual network segments [3]
By the use of computer simulation, data were obtained on the difference between the duration of the fight and the time of the helicopter [Δt]. Based on the obtained data, 3-D graphs for case I1 were made:
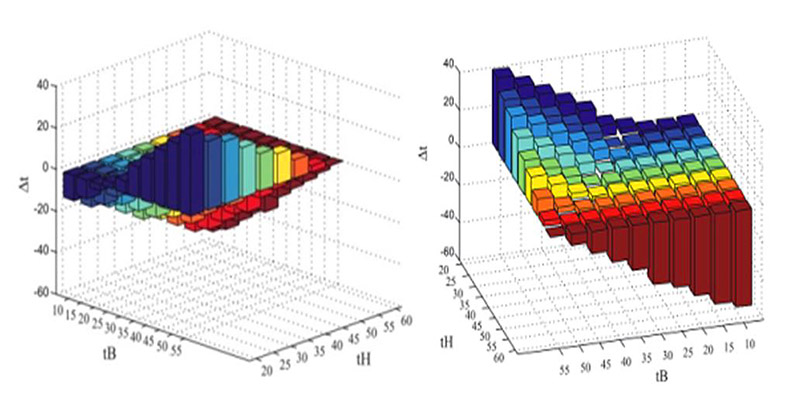
Chart 1. Displays the time difference [Δt] between the duration of the combat [tB] and the helicopter (tH) time for scenario I1 [3]
Based on the developed and analyzed case of the dynamics of the pirate attack on Petri's nets with a pirate ship accompanied by a warship (helicopter), with the same analogy, a scenario simulation of two and three pirate ship attacks was made.
Pirate Attack Risk Assessment [3]
Based on certain factors of the success of the pirated attacks, a risk assessment methodology can be developed using a Qualitative Risk Assessment Methodology. Method II - Risk rating assessment was used to calculate the risk assessment. After identifying the threats, the Threat Probability P(T) and the Threat Impact - I(T) are estimated.
To assess the risk level, a Risk Indicator is selected:
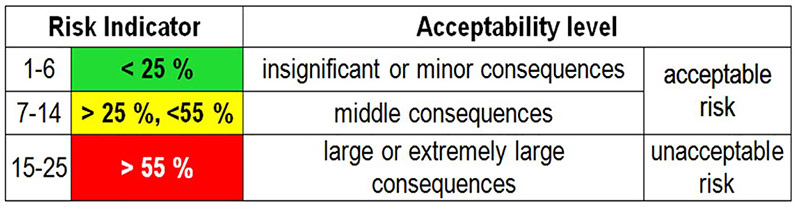
Table 1. Risk Indicator
The level of risk acceptance is determined individually for each investigated case study. It is determined by an interested client after evaluating all the risk factors used. Once the risk indicator and the level of acceptability according to Table 24 have been determined, the Information Technologies Project Risk Assessment Report (University of Calgary) [22] was used as the basis for risk assessment.
Based on the obtained results, ship risk level, and in order to optimize ship passage planning through the navigable areas of possible pirate attacks of the "n" ship strategy selected six strategies (B1, B2, B3, B4, B5 and B6).
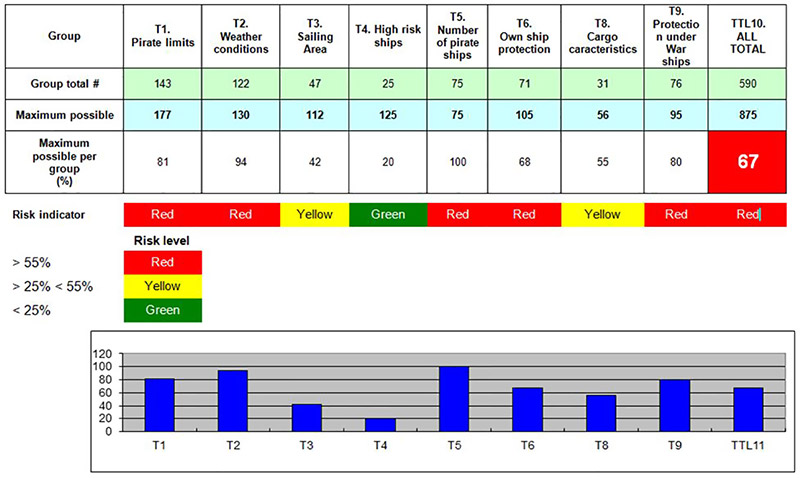
Table 2. BTTL Calculation of the individual and total ship risk levels with B1 [3]
The individual and the overall level of pirate ship risk was calculated according to the performed quantification of the results of conducting attacks for pirate ship.
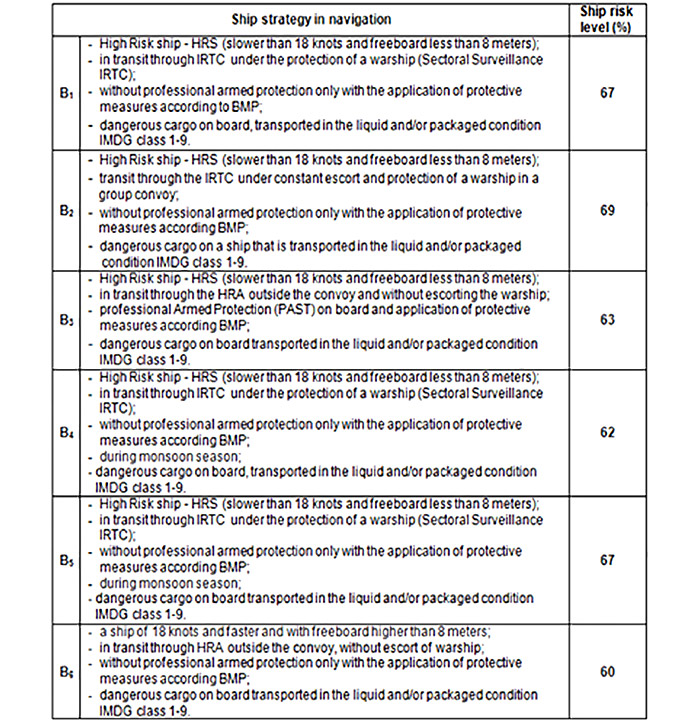
Table 3. Ship Strategy [3]
Pirate Risk Assessment [3]
Pirate risk assessment is based on the same methodology as the risk assessment for the ship in navigation. Therefore, any aggravating circumstances to our own ship at sea during pirate attacks are at the same time, mitigating circumstances for pirates and vice versa. In other words, reducing the consequences for the ship during the pirate attack with one pirate ship, at the same time increases the consequences for pirates. This means that in the attack on the ship at sea with one pirate ship, increases the risk of pirates and reduces the risk of the ship, while increasing the number of pirate ships in the attack increases the risk for the ship, and reduces the risk for pirates because the possibility of taking over the ship is higher, and the possibility of the defence of the ship is lower. Therefore, individual and the overall pirate risk levels were calculated for attacks with one (I1), two (I2) and three (I3) pirate ships, using readymade tables of quantification of results (threats) for a pirate ship and its ranking values of T1, T2, T4, T5, T6 (individual risk level calculation) and ITTL10 (total risk level calculation) of a pirate ship (I1-I3).
According to the performed quantification results for the ship individual and the overall risk level was calculated during a pirate attack on ship in navigation through pirate attacks risk areas as follows:
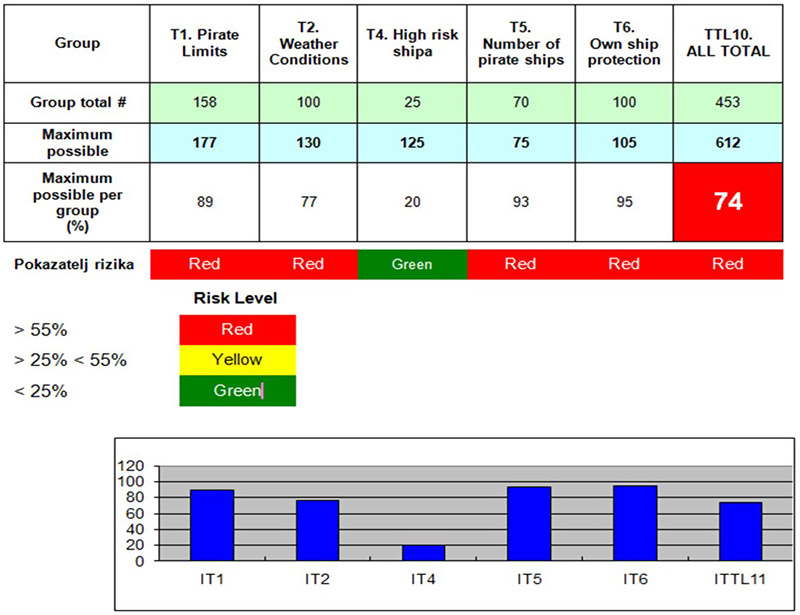
Table 4. ITTL Calculation of the individual and total pirate attack risk levels with I1 [7]
Based on the obtained levels of risk, three pirates strategies (I1, I2, I3) are determined in relation to the possible success of such attacks expressed in percentages (%).

Table 5. Pirate Strategy [3]
From the results of the ship's risk level (B1, B2, B3, B4, B5 and B6), and the pirate risk level (I1, I2, I3) the model of the ship behaviour was developed compared to pirate activities. In making decisions on choosing the best ship strategy (B), shown through the applied Game Theory model, solved by the Simplex method of linear programming.
Ship Protection against Piracy Attacks
The selected problem of designing the ship's protection model against piracy is complex, and its complexity stems from the following:
- Complexity and incompleteness, uncertainty and conflicting knowledge about how to define and achieve goals;
- A large number of parameters affecting the decision;
- There are more decision-makers who have different perceptions of the problem and may have conflicting goals;
- Time constraints for the decision process.
Appropriate mathematical models can be developed to determine the strategy for the ship’s behaviour in relation to possible pirate activities during the ship's passage through the piracy risk areas. The goal of this model is to contribute to the development of the ship's strategy in optimizing navigation in the pirate area.
Accordingly, different ship strategies can be developed as well as the methods of action in different situations in which the ship and crew are exposed while sailing in pirate areas. One of the ways to look for such solutions is Game Theory. Game Theory is a mathematical theory and methodology used to analyze and solve conflict and partially conflict situations in which participants have conflicting interests [26]. In order to develop Game Theory at least two players will each need to make meaningful and planned decisions to achieve the maximum score/gain in the end. Therefore, it is said that every simple planning activity is a "game" and it is opposed to uncontrolled activities, because in that case, there would be no game.
Consideration of situations in which two or more subjects make decisions in the situation of conflict of interest is called Game Theory. Typical examples of such situations represent different antagonistic situations such as the defence of the ship against pirate attacks. It should be emphasized that Game Theory methods serve to analyze and solve such conflict situations characterized by multiple repetition of certain decisions on the possible resolution of conflicts of interest between the participants (opponents ), i.e. the player [14], [15].
Ship Model Behaviour with Respect to Pirates Activities
Based on the above analysis as well as in practice, it is known that the success of the defence of ships against pirate attacks depends on the type and size of the ship, its speed and freeboard, speed of the ships in the convoy, the presence of a warship, the level of PMSC and / or APMSC protection, limiting factors of the pirates to give up on the attack on the ship. The success of the defence of ships against pirate attacks also depends on whether the pirates attack with one, two, three or more pirate ships, the direction from which pirates approach the ship during the attack, weaponry, the limiting
factors of the pirate to attack the ship, etc. Each of these options or variants is called the strategy. So the ship can have more different strategies Bi, and the pirate has a strategy Ij. That number is denoted by eij mathematical expectation) where eij :
mij number of successful defences
nij the number of all attacks
Thus, for finding all values of eij a matrix table E is formed. To determine the best strategies, Game Theory is used according to John von Neumanna's criterion [15]:
One of the most effective ways of solving this problem is the Simplex method of linear programming . If we divide all inequalities with W and enter mark pi/W=xi , a qj/W=yj, then we get the following two models [26]. Every linear programming problem (primary problem) has its dual problem.
Coefficients of the objective function of one problem make the right side limitations of the other. Each free variable corresponds to the condition with the equality sign (artificial variable), and for each artificial variable there is a corresponding free variable.
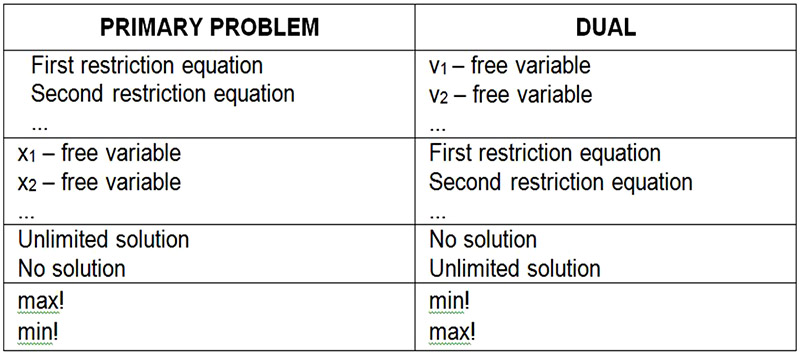
Table 6. Rules for computing duals
Source: Zoran, Babić: Linearno programiranje, Ekonomski fakultet Split, Split 2010. [14]. Barković, Dražen: Operacijska istraživanja, Ekonomski fakultet Osijek, Osijek 2002. [2].
By solving the second model as the primary, the first model solution of the dual model is obtained. Starting table to solve the problem is as follows [14], [16]:
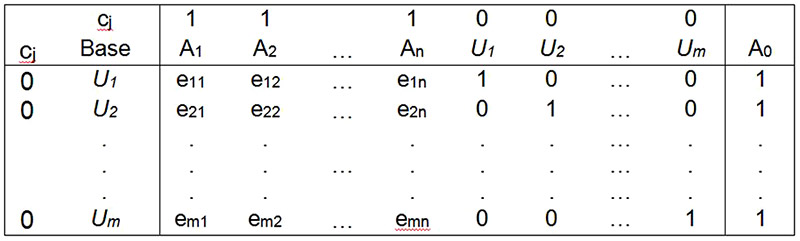 Table 7. Solving the model by the use of linear programming Simplex method. Source: John von Neumann, Game Theory, 1928.
Table 7. Solving the model by the use of linear programming Simplex method. Source: John von Neumann, Game Theory, 1928.
The interactions of the table give the optimum solution, ie. Zmax=Z*,
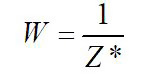
y1*, y2*, …, yn* which are located in a given column, while in a given row below U1, U2,…, Un the optimal solutions for the first model can be found.
From the theoretical basis of linear programming [2] it is known that:
Zmax=Zmin=Z*, (4)
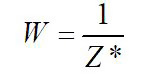 (5)
(5)
Value of the game is
qj=yj*•W (6)
pi=xi*•W (7)
(If we want to express the values in percentage, then we multiply all by 100.)
The aforementioned values of selected pirate strategies I1, I2 i I3 and ship strategies B1, B2, B3, B4, B5 and B6 were applied in Game theory in order to select the behaviour of a shipping company in relation to pirate activities. Table 8 shows the expectations of the game for ship strategy (B). [3]
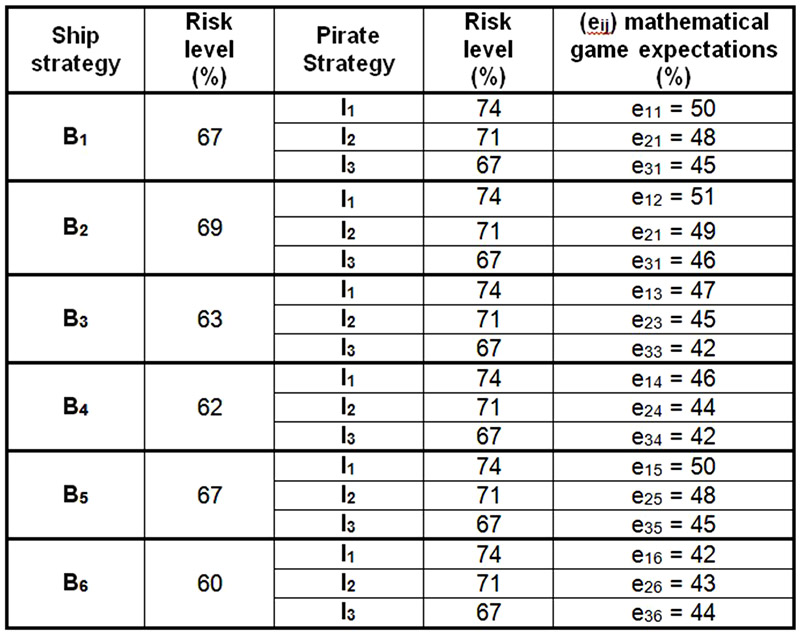
Table 8. The Effect/Value of the game for strategy B [3]
By taking these assumptions into account, the data for Game theory are obtained and shown in the table; a tabulation of the results obtained is a matrix E.
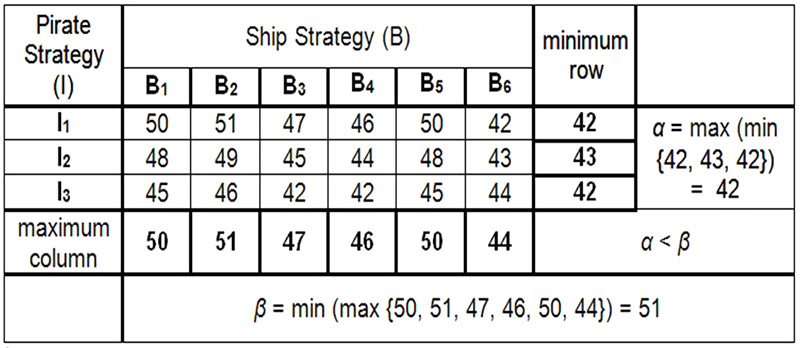
Table 9. Matrix E Game Theory [3]
Table 10. Appearance of the matrix E in the computer programme WinQSB2.0 (Quantitative System for Business) [3]
Since α ˂ β does not have a saddle point, it is a mixed game, and the biggest loss of players in Game Theory (the shipping company, the pirate) is the value of the W game, which ranges between 42% and 51%.
The value of the game is determined by the probability q1, q2, q3, q4, q5, q6 that the ship (B) selects/uses strategies B1, B2, B3, B4, B5 or B6, respectively p1, p2, p3 the pirate (I) choose/use strategies I1, I2 or I3. In that case, the probability is that each of them will apply only one strategy to ensure that its gain/loss is the highest W.
The calculation of the optimum ship solution by Simplex method computer programme WinQSB 2.0 (Quantitative System for Business), we get the following:
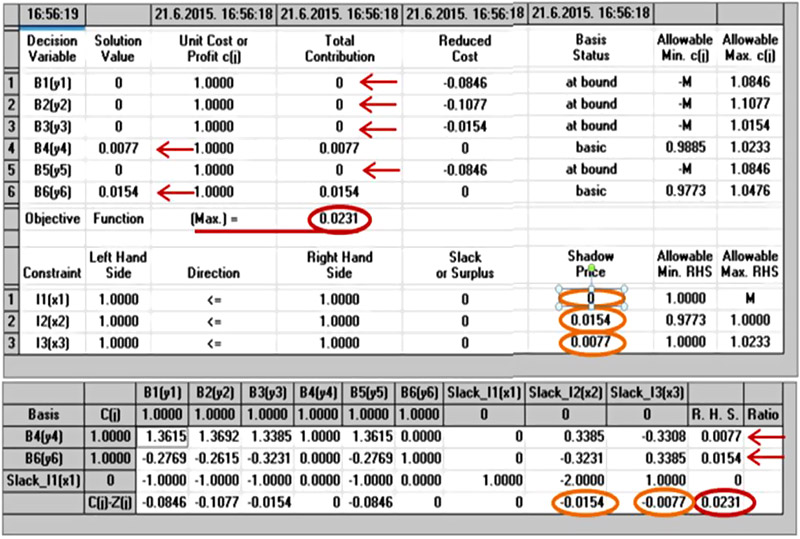
Table 11. Calculation of the optimum ship/pirate solution using Simplex method computer program WinQSB2.0 (Quantitative System for Business) [3]
(Note: Programme calculated values are expressed as negative because they count in reverse order C(j)-Z(j) )
From Table we read the following:
According to this calculation in an optimal case, the ship (B) should be using the strategy B6 in approximately 67% of cases and in approximately 33% of the cases with Strategy B4, while strategies B1,2,3,5 would not be used at all.
Pirate strategy:
Pirates (I) should use strategy I2 in approximately 67% of attempts, and in approximately 33% of cases strategy I3, while strategy I1 would not be used.
Results Analysis of The Use of Petri Net Model, Risk Assessment and Game Theory Model [3]
As a result of a series of simulations using the Petri nets, the results of various pirate attack scenarios were investigated with one, two, and three pirate ships with a ship in navigation accompanied by a warship with a helicopter. This allows the simulation of the traffic through pirate area and consideration of the pirate attacks dynamics. The appropriate hybrid Petri nets and computer simulation had been developed and used for each scenario. The time dynamics of events was analyzed and graphically displayed for all three case studies, a way that in all three cases different time duration of the fight was evaluated between pirates and their victim – the ship. The simulation considers the variables that are constantly changing in time (distance and speed) and variables that change discreetly in time (the pirate during the attack, the fight, etc.). The time dynamics of pirate attacks was made by using the "VisObjNet 27a 500 ++" (Visual Object Net) tools which enable modelling and simulation of continuous and discrete (hybrid) Petri nets. These tools are not intended for modelling and simulation of stochastic but for deterministic processes only, so every analysis in this direction requires a change of software. The activities of defence and the activities of the ship can be further developed and proposed based on the results of the simulations obtained by Petri nets. Existing simulation could be taken further by introduction of additional discrete and continuous places and transitions by introducing additional factors that directly affect the activities of the pirates during the attack. Thus, a further developed model could be used for precise planning at the level required for the defence merchant ship.
In the situations regarding the increase of the ship defence success against potential pirate attacks it is necessary to make timely and proper decisions. The consequences of these decisions and actions may depend solely on one party, but they also depend on the interaction with the decisions and actions taken by the other party. The interests of these parties are often in conflict. Therefore, the methodology of the risk assessment of the ship and the pirates was developed, and the application of the proposed model of Game Theory solved by the Simplex method of linear programming (the software program WinQSB2.0 of the Simplex method of linear programming was used in finding solutions). Based on this theory, the mathematical process of scientific prediction and planning was worked out taking into account optimal own and opponent's moves (strategy). Solving this problem is much more complicated and it becomes complex if a large number of different factors are involved in the calculation, and when there is more than one participant in the game. The importance of this program stems from the fact that the problems of linear programming, relevant to practice, must take into account a number of circumstances that are so complex that in numerical solutions they require a great amount of calculating which can be solved only by means of a computer.
Nowadays, the Game Theory model has become widespread and it is used for modelling conflict situations in mathematics, politics, economy (business economics), military strategy, etc. Apart from using this model directly to determine one of the most important factors of an optimally safe ship passage, it could also be used by private users in solving transport network problems, off-shore terminals for planning the level of protection and terminal operations in the event of unauthorized access to the terminal's facilities, port terminals and the Port Authority for assigning ship’s unloading/loading places, towage services and others.
Conclusion [3]
In this work, the Petri Net was used to develop the time-dynamics of the pirate attack on a ship sailing through the area protected by a warship with a helicopter. A Time Hybrid Petri Net was used in the analysis of piracy attacks for the first time, allowing simulation of very complex, continuous and discrete processes. The simulation model can be used as an objective measure for assessing the state of the ship's protection in the vulnerable water area when planning measures and activities to improve the ship's safety and protection against possible piracy attacks. This further developed model could serve for a precision planning of the required level of merchant defence and a helicopter activation time.
Furthermore, the possibility of preventive protection of the ship from potential piracy attacks and risk assessment of the ship have been systematically processed. In order to facilitate the selection strategy and decision-making by the master of the ship, a risk assessment methodology was made for the ship navigating through the areas of possible pirate attacks. After the risk assessment level has been made in case of a pirate attack on a ship with one (I1), two (I2) and three (I3) pirate ships, the various ship operation options (B) are determined. Then we considered the proposed ship of high risk in navigation and determined the six possible strategies of the ship (B1, B2, B3, B4, B5, B6, …. Bn).
The developed model of Game Theory selects the best strategy of a ship in planning the level of protection of the ship in navigation through areas of possible piracy attacks. The developed and proposed model is an open type model. It allows the introduction of new, currently unknown and publicly unavailable factors. The model is dynamic, in time upgradable and self-learning. The advantage of the presented model of Game Theory is in its flexibility. The model can continually expand to as many new relevant factors as the system user wants at any given time.
References
1. The Baltic and International Maritime Council (BIMCO), 2011.
2. Barković, D. (2001), Operacijska istraživanja, Ekonomski fakultet Osijek.
3. Belamarić, G. (2015), Doctoral thesis, Model for ship protection against Piracy attacks, Faculty of Maritime Studies, University of Rijeka, URN:NBN https://urn.nsk.hr/urn:nbn:hr: 187:648635.
4. Chinese Association for System Simulation (CASS) (2012), The International Journal of Modeling, Simulation and Scientific Computing (IJMSSC), World Scientific Publishing Co. http://www.editorialmanager.com/ijmssc/default.asp).
5. Grabovac, I. (2012), Piratstvo i sigurnosna zaštita brodova hrvatske državne pripadnosti, Pravni fakultet, Sveučilište u Splitu. Pregledni članak 8. 6., Split.
6. Grabovac, I. (2013), Uvjeti za pravne osobe koje pružaju usluge ukrcaja osoba za naoružanu pratnju na brodove hrvatske državne pripadnosti kao zaštita od piratskih napada i oružane pljačke, Kapetanov glasnik br. 26., Udruga pomorskih kapetana, Split.
7. Hans Liwång Chalmers, Jonas W. Ringsberg Chalmers, Norsell, M. (2013), Quantitative risk analysis – Ship security analysis for effective risk control options, Swedish National Defence College, Stockholm.http://urn.kb.se/resolve? urn=urn:nbn:se:fhs:diva-3800;http://fhs.diva-portal.org.
8. Il Messaggero, (2015), Ministry of defense Republic of Italy, Piraca in Mediteranean Sea.
9. IMB-ICC Piracy & Armed Robbery Map (2014), Prikaz piratskih aktivnosti po područjima svijeta,.: www.icc-ccs.org/piracy-reporting-centre/live-piracy-map/piracy-map
10. Babić, Z. (2010), Linearno programiranje - drugo izdanje, udžbenik Sveučilišta u Splitu, Ekonomski fakultet Split.
11. LU Yan-Jun, DAI Hua-Ping (2012), Hybrid Petri net modeling for urban traffic network, Journal of Zhejiang University (Engineering Science 2007-06) Hangzhou, China), State Key Laboratory of Industrial Control Technology, Institute of Industrial Process Control, Zhejiang University,http://en.cnki.com.cn/Article_en/CJFDTOTAL-ZDZC200706011.htm.
12. Ministry of defense Republic of Italy (2015), ISIL arriving in Evropu, Piracy Threat in Mediteranean: http://www.vijesti.me/svijet/isil-dolazi-u-evropu-mediteranu-prijeti-piratstvo-820019.
13. NATO COUNTER-PIRACY OPERATIONS, NATO (2015): http://www.nato.int/cps/en/natohq/topics_48815.htm.
14. Nash, J. (1951), Non-cooperative games, Annals of Mathematics Vol. 54, 286-295. USA.
15. Neumann, von J. (1928), Game Theory Criterion John von Neumann, USA.
16. Neumann J. von, Morgenstern O. (1947), Theory of Games and Economic Behavior. Princeton University Press, USA.
17. TEORIJA IGARA: https://www.google.hr/?gws_rd=ssl#q=4.
18. Steamship Insurance Management Services Limited (2010), Piracy from the P&I Perspective, San Francisco.
19. Tsilis, T., Lucas T. (2011), Counter-Piracy Escort Operations in the Gulf of Aden, p. 68-71., Naval Postgraduae School, NATO Maritime Interdicton Operational jourrnal.
20. René D., Hassane A. (2010), Continuous and Hybrid Petri Nets, 2nd ed. 2010, XXII, 550 p Discrete, Springer-Verlag Berlin and Heidelberg GmbH & Co. K, Berlin.
21. SOLAS Consolitaded text of the International Convention for the Safety of Life at Sea, 1974, and its Protocol of 1988: articles, annexes and certificates, IMO , SOLAS – Consolitadated Edition 2001. London, 2001.
22. University of Calgary. Information Technologies Project Risk Assessment Report (2012) - (Project Risk Assessment Report.19.20). www.ucalgary.ca/.../risk_assessment%2008feb12.xls.
23. United Nation - UN, The United Nations Convention on the Law of the Sea, International Convention on Open Sea, Ženeva, 1958.
24. United Nation - UN, The United Nations Convention on the Law of the Sea 1982., – UNCLOS, National Gazzete – International Contracts, br. 11/95, 9/00), Zagreb.
25. United Nation - UN, UN Reports of the Secretary-General on Piracy, Security Council Resolutions, Document Title, od 2001. do 2012. London, 2012.
26. United Nation - UN, United Nations Convention on The Law of the Sea 1982., The ratification of maritime convention, Part II.1, Public International Law, Lloyd's of London Press, norme o piratstvu čl. 100 - 107, London, 1982.
27. (97) United Nation - UN, Security Council Resolution UN-a: 1814, 1816, 1838, 1846, 1897 i 1918., London, 2008. & 2010.
28. Witherby Publishing Group Ltd. (2011), ”BMP-4 – Best Management Practices for Protection against Somalia Based Piracy”. http://www.cusns.navy.mil/marlo/Guidance/BMP4web.pdf.
29. Young, T. (2012), Piracy hot by spot: http://www.avvo.com/legal-guides/ugc/top-4-piracy-hot-spots-in-the-world-today.