Fundamentals of the Comprehensive Use of Military and Non-Military Forces and Means to Counter the Hybrid Aggression
(Volume 23, No. 2, 2022.)
A. Syrotenko, Dr. habil, The Head of the National Defence University of Ukraine named after Ivan Cherniakhovskyi, Kyiv, Ukraine, ORCID https://orcid.org/0000-0002-0266-5706
Colonel V. Semenenko, PhD, The Deputy Head of the Center for Military and Strategic Studies of the National Defence University of Ukraine, Kyiv, Ukraine
Izvorni znanstveni rad (Original Scientific Paper)
Received: 25 October 2021
Accepted: 1 March 2022
DOI: https://doi.org/10.37458/nstf.23.2.1
Abstract
The article is devoted to the problematic issues of determining the strategy of using military and non-military forces and means to counter "hybrid" aggression. The principles, goals, forms and methods of integration of military and non-military forces and means of counteraction are defined. The article proposes the Concept of integrated use of military and non-military forces and means to counter "hybrid" aggression (threats of "hybrid" type)
Keywords: Hybrid warfare, Ukraine, Russian Federation, Military power

Introduction
A systematic approach to ensuring the military security of the state requires a significant clarification of views on the role of central executive bodies and other institutions of state power in combating military and hybrid threats. At the stages of the emergence and exacerbation of the military conflict there is an intensive use of political-diplomatic, economic, information-psychological, legal and other measures against state institutions of power. At this time, the role of the armed forces is ancillary and is to deter the opposing side from making hasty, reckless decisions aimed at resolving disputes by force.
The problem of finding effective methods of resolving military conflicts is relevant and is of great importance for strengthening the military security of any state. Neutralization of military and hybrid threats through military measures is achieved by material damage to the opposing side in various areas. At the same time, military measures have a greater impact on the conflicting parties. However, the biggest disadvantage of military measures to neutralize military and hybrid threats is that their use is associated with high material costs of economic potential and losses among the armed forces and civilians. Therefore, there is a need for integrated use of military and non-military forces and means to counter hybrid threats.
Shifting of military conflicts emphasis to the asymmetric use of military force by extralegal armed formations, comprehensive use of military and non-military tools (political, economic, informational, psychological, etc.) is fundamentally changing the nature of armed struggle and making new demands on the military security system .
Purely military tools become ancillary to achieving military-strategic objectives set by the aggressor. Prior to the armed conflict, the aggressor’s main efforts were to destabilize the socio-political situation, provoke public dissatisfaction with the current government, incite separatist sentiments in society, and discredit the country’s military-political leadership targeted by the aggressive actions. All this created a basis to actively and covertly form a so-called resistance movement, establish special paramilitary units and train them in methods and techniques (including the use of weapons) that should be used to resist the current government. As a result, the state reacts violently to terrorist acts and provocations, including the use of force. The aggressor presents this reaction internationally as the suppression of democracy or the rights and freedoms of citizens of certain regions or national minorities. Combination of different instruments (military and non-military) and using them as an excuse for an aggression against another state determines its hybrid nature.
Specific sequence of modern military conflict development stipulates a need to define principles, forms and methods of integration of state’s military and non-military forces and means of countering the armed aggression which had hybrid nature.
Principles, Aims, Forms and Methods of Integration of Military and Non-Military Counteraction Forces and Means
Under current conditions, capabilities of the armed forces of the world’s leading countries to collect, process and distribute information has increased significantly. Information has become an important factor for changing the rules of war in favor of widespread use of non-military tools to achieve war strategic aims. These tools determine the use of political, economic, informational, humanitarian and other methods that intensify the society’s protest sentiment and are combined with the undeclared (and / or covert) use of military forces and means. Aggressor countries no longer rely on classic invasions but achieve their aim through a combination of special (subversive) operations, cyberattacks, carefully planned actions aimed to destabilize the situation, disorganize governance and military command and support illegal armed groups in enemy territory.
In this context, settlement of an armed conflict is considered as a process of coherent interaction between international structures responsible for international security and peacekeeping as well as for security and defense sector components that can be targeted at protecting national interests in order to take all possible actions and measures conducted simultaneously or sequentially to solve issues that have led to unleashing the conflict.
To counter the destructive pressure of the aggressor on Ukraine and force it to comply with international law and its own obligations, the state’s doctrinal documents stipulate “coherent use of state’s political, diplomatic, informational and force instruments.” In light of new, more varied and covert mechanism of emergence of the armed conflict demonstrated by the Russian Federation in unleashing the armed aggression against Ukraine, joint and coherent use of military and non-military forces and means is a key precondition to resolve it. This requirement derives not only from the intent to avoid duplication of tasks assigned to individual security and defense sector (SDS) components in settling the conflict and prevent misuse of resources, but also from the fact that the role and place of military means themselves is changing during the countering the hybrid aggression. The experience of resolving the armed conflict in the East of Ukraine has shown that successful countering the hybrid aggression is impossible without integration of state’s military and non-military forces and means .
Despite the declared need to integrate efforts (to join involvement) of the SDS components, it has not yet been determine how to arrange the integration process (i.e. integration technology). This indicates an emerging scientific and organizational problem. Therefore, determining the aim, forms and methods of integration of SDS military and non-military forces and means to counter military threats with signs of hybridity can be considered one of the stages in solving the above mentioned scientific problem. Complexity of its solution requires a systemic interdisciplinary and general scientific approach aimed at integrating the achievements of social, natural and technical sciences as well as practical experience, especially in the field of organization and management.
Governing documents on national and military security of Ukraine guide state’s security and defense sector entities towards the priority use of soft power structures and non-military measures to eliminate or neutralize threats of a military nature. At the same time, armed struggle remains an important factor that influences the results of military conflicts and remains the key factor in addressing topical defense issues.
Existing ways of resolving armed conflicts intend, first of all, to develop armed forces, increase defense forces capabilities and implement a set of measures (development of operational infrastructure, mobilization, operational deployment of troops (forces), etc.) aimed to prepare and conduct defense actions, localize a conflict zone (area), neutralize IAF, etc. This does not fully correspond to the real conditions in which the armed conflict emerges and develops. The role and place of the force component in countering hybrid threats can vary significantly depending on the phase of conflict development. Thus, the role of integrating efforts of military and non-military security and defense sector entities in countering military threats of a hybrid nature is growing.
According to military analysts, the ratio of the contribution of military and non-military means in achievement of military-political objectives of the armed conflict has changed significantly in favor of the latter. The contribution of military and non-military means also changes during different stages of the armed conflict . This necessitates their prioritization and development of practical recommendations on integrating efforts of military and non-military Ukraine’s security and defense sector entities to neutralize military threats with the signs of hybridity.
The armed conflict in the East of Ukraine is characterized by the asymmetric use of military force by extralegal armed formations. The parties to the conflict use mercenaries (including foreign ones) and volunteer battalions staffed with both patriotic citizens and criminal elements. Emphasis shifted on the simultaneous and coherent use of military and non-military instruments (economic, political, informational, psychological, etc.). This fundamentally changes the nature of the armed struggle and puts new demands on the military security ensuring system.
Existing ways of building national security and defense capabilities are also generally focused on the joint use of the security and defense sector forces and means. At the same time, there is a need to clarify principles, forms and methods of integration of military and non-military forces and means with due account for the experience of countering the hybrid aggression of the Russian Federation.
Analysis of the main trends in the world’s security environment proves that the vast majority of the trends stipulate the use of military force as an important argument in relations between countries. However, it is not force but informational, socio-political, ideological and economic components of influencing the enemy to achieve military-political objectives in an armed conflict unleashed as a result of hybrid aggression that move to the forefront.
Purposeful nature of military threats adaptive to the state under aggression and based on a combination of military and non-military measures is considered the main sign of their hybridity . It is the purposeful nature and high dynamics of threat transformation and combining informational, socio-political, ideological, economic and military aspects of influencing the enemy that needs careful preliminary elaboration at the state level with development of appropriate measures to adequately counter them.
In light of this, it is possible to formulate the main aim of measures to counter military threats of hybrid nature (with signs of hybridity): timely revealing of a threat in a particular sector of society and the state life covered by the state’s military security system and threat’s possible consequences for ensuring national security and preventing transformation of the threat from potential to real through elimination of its forming factors .
That is, threats of a military (and hybrid) nature formed not by purely military but rather non-military factors require equally comprehensive response. Military threat hybridity is evidenced by hidden, purposeful, destructive and comprehensive influence on the national security system, i.e. in a set of both military and non-military factors (intentions and actions) integrated by a single aim. Therefore, efforts of military and non-military forces and means should be integrated (integrated counteraction potential should be formed) to prevent such threats . The implementation of this counteraction is entrusted to the security and defense sector of Ukraine.
The integrated potential for counteracting military threats with signs of hybridity means the formed rational composition of SDS forces and means and determination of their necessary capabilities, planned for implementation according to a single plan to de-escalate the identified (predicted) threats of comprehensive (hybrid) nature within the resources allocated by the state and NGOs.
Currently, it is generally defined how to organize the integration process (integration technology). A method of forming and managing the integrated countermeasure potential has been developed, but it should be practically implemented in the form of recommendations to central executive and military administration bodies with due account for their future model. The essence of the method is based on the hypothesis that the identified or predicted level of threat, including of a hybrid nature, should be neutralized primarily by non-military (political, economic, information-psychological, etc.) methods and means, and in case of their low efficiency – with the use of military-political, military-technical, special, defense and other actions to ensure a sufficient level of state military security . This will allow substantiating a rational composition of forces and means and their capabilities necessary to de-escalate the identified threats within the allocated resources. And here lies an emerging scientific and organizational problem.
Determining the aim, forms and methods of integration of SDS military and non-military forces and means to counter threats of a hybrid nature can be considered as one of the stages in solving the above mentioned scientific problem. The complexity of its solution requires a systemic approach of interdisciplinary and general scientific nature aimed to integrate achievements of social, natural and technical science, as well as practical experience, especially in the field of organization and management. This, in turn, requires to consider a possible combination of military and non-military SDS forces and means of countering military threats especially with hybridity signs) as a system . Formation (synthesis) of this system and its integrative qualities should be based on its purposefulness as a system-forming factor.
The above-defined aim of such a system as an objective criterion for selecting all its forming elements and relations from among all the elements and relationships of the environment will determine a necessary composition of SDS entities and their functions. Further decomposition and formalization of the aim give opportunities to correctly describe it.
To do this, we propose to develop a more detailed formulation of the aim of integration of military and non-military forces and means. This will help synthesize a system of measures which would be able to effectively counter threats, including those of a hybrid nature. In fact, we are talking about creation of an appropriate system of countering such threats in the military field .
It is proposed to use SDS capabilities necessary to counter threats of a “hybrid” nature according to a single plan, most commonly in the form of a special de-escalation operation within the resources allocated by the state and NGOs.
Therefore, considering the essence of military threats with signs of hybridity, the aim of integration of military and non-military forces and means of counteracting these threats is such an organizational combination of forces and means of SDS entities which, if used under unified leadership and appropriate planning, would be able to effectively reduce the impact of factors which form the threat to acceptable values. Decomposition of this aim using one of the methods of building a system of objectives – building a “tree” of objectives (sub-goals) to combat military threats – will allow to reveal relationships between objectives of different levels, break them down into stages and provide a clear picture of the system of objectives.
The number of key aim components (sub-goals) and their hierarchical levels will depend on the chosen strategy of countering the threat, abilities of the SDS entities and their subordinate structural divisions involved in counteraction. Such a “tree of objectives” links long-term and short-term objectives allowing to see the overall strategic picture of countering threats. The following types of objectives can be distinguished:
1. Strategic, which are formed while defining a long-term process of countering threats;
2. Tactical, which are formed to solve operational tasks by SDS entities;
3. Trajectory, which determine a general direction where the subject of influence (a factor or a group of factors that form the threat) should change.
While forming a “tree” of objectives, such basic requirements as exclusion of unimportant and ineffective measures as well as measures hampered by insufficient resources shall be met.
The main system requirements for the list of sub-goals of the lowest level are classical: their completeness, sufficiency and measurability. It is the measurability of the objectives that makes it possible to find a rational distribution of efforts among the SDS entities and organize their performance control at all stages of countering threats of a hybrid nature.
However, in view of peculiarities of the SDS entities (with different functions and subordination in the general system of state bodies, the presence of NGOs), measurability of objectives is expected to be very difficult to ensure because in contrast to technical and organizational systems, the newly-formed system of countering hybrid threats includes both military and non-military forces and means.
Therefore, the formation of a “tree” of objectives will be decisive in organizing the process of integration of military and non-military forces and means.
Based on the above, the basic principles of the integration of military and non-military forces and means for countering threats of a hybrid nature can be enunciated:
1. Systematicity – is embodied in the aim of countering threats and implies obtaining an emergence effect from the integration of military and non-military forces and means;
2. Adequacy to the threat – requires compliance of the involved SDS entities, their assigned tasks and allocated resources with factors that form the threat;
3. Optimized distribution of efforts and various resources among the involved SDS entities and;
4. Scientific approach to the formation of the integrated potential of military and non-military means – it obliges to comprehensively analyze threats and ensure validity of countermeasures on the basis of complete and reliable information with the use of scientific methods and approaches and modern software ;
5. A principle which unites a group of managerial principles that relate to organizational and managerial decision-making. It is adherence to the managerial principles that ensures achievement of the aim of countering threats. These key principles proposed for consideration are:
6. Only one control center (body);
7. Balance of rights and responsibilities of decision-makers in the SDS entities structure, that is, their responsibility should be consistent with their powers;
8. Feasibility of the designated tasks and deadlines;
9. Cost-effectiveness, i.e. due account for various kinds of available resources and their congruence with the specific aim;
10. Flexibility, i.e. the ability to change according to the already obtained intermediate results and the environment;
11. Specificity and targeting; this imply defining an executor, time and deadlines of an event;
12. Consistency, i.e., coherence with other decisions on ensuring military security;
13. Completeness of the content (as a system principle), i.e. a decision should cover a threat in general, possible lines of its development, means and resources used to achieve objectives of countering the threat, deadlines, the order of interaction between the SDS entities at all stages of counteraction;
14. Prediction of risks and an intent to reduce them to the minimum possible level; this requires risk management, i.e. early detection of uncertainties and forecasting consequences of their impact on functioning of the SDS to develop and implement solutions to mitigate them.
It should be noted that countering hybrid threats is a complex process due to a large number of heterogeneous factors shaping these threats and difficulties in predicting changes in the intensity of their impact.
While considering possible forms and methods of integration of military and non-military means to counter military threats with signs of hybridity, the term “integration” can be considered from several points. Firstly, integration can be a purposeful cohesion of some entities into a single whole for joint activities (purely organizational task). Secondly, it can be joint activities of some entities with the appropriate purpose.
Because cohesion of entities to ensure national security already formally exists in the form of the SDS, it is the joint activities of its entities that are considered as a countermeasure to military threats with hybridity signs. Such activities of the SDS entities require to define appropriate forms and methods of counteracting such threats. In choosing ways of integration, the following becomes decisive:
1. Abilities of forces and means that will be involved in the counteraction within the framework of integrated efforts;
2. Qualitative characteristics of personnel which will be responsible for development of both general strategy for countering the threat and development and implementation of tasks at the SDS entities level .
Summarizing all the above, several basic ways to integrate military and non-military means of countering military threats can be proposed:
1. Integration of military and non-military forces and means with priority of soft power and supportive use of force;
2. Integration of military and non-military forces and means with priority of force and supportive use of soft power.
It is clear that each of these integration methods can have many options for the composition of forces and means of the SDS entities used and the degree of their participation in countering the threat over time. Deeper consideration of ways to integrate military and non-military forces and means to counter military threats with signs of hybridity requires further research.
As for the forms of integration of military and non-military means to counter military threats with signs of hybridity, it is proposed to adopt the military terms “operation” and “campaign”. The meaning of the term “operation” has no practical difference from that used in the art of war (“coordinated actions of mixed forces and means consolidated by a single aim”).
As for “campaign”, peculiarities of hybrid threats as a subject of inquiry and complexity of counteracting them give grounds to use this term despite it is almost no longer used. As noted above, threats of a hybrid nature are formed by many factors which impact is characterized by: large scale; usually significant time frame; focus on various state institutions and entities which functioning affects the level of the state of defense, etc.
It is clear that an adequate response to such threats also requires significant time, involvement of a large number of SDS entities (and not only them) as well as financial and material resources in the counteraction. The adequate response is impossible to accomplish as an operation because the latter has a more specific and timed-constrained nature. Therefore, in our opinion, it is quite correct to denote a reaction to threats of a hybrid nature by the term “campaign”. That is, a “campaign” becomes the form of achieving the strategic aim of countering military threats including those with signs of hybridity. The operation as a form of achieving one of the tactical objectives of counteraction then becomes its component because it is more local, specific in aim and objectives, and, therefore, limited in time, participants, and a form of integration of military and non-military forces and means. Countering the threat in the form of a “campaign” will then consist of a set of operations (actions and measures) of different types and scopes, consolidated by a common strategic plan. This corresponds to the classical understanding of the term.
Given that military threats, especially those of a hybrid nature (with signs of hybridity) are formed by many heterogeneous factors, the content of forms and methods of integration of military and non-military forces and countermeasures can have a large number of options. In order to practically implement the determined forms and methods of integration of military and non-military forces and means of counteraction, it is advisable to have a concept of their comprehensive use which main provisions are set out in the next section.
The Concept of the Comprehensive Use of Military and Non-Military Forces and Means to Counter Hybrid Aggression (Hybrid-Type Threats)
The comprehensive use of military and non-military forces and means implies formation of an integrated potential to counter threats which refers to the most rational composition of SDS forces and means with their defined necessary capabilities. The capabilities shall be implemented according to a single plan, usually in the form of a special operation to de-escalate the revealed (predicted) hybrid-type threats within the resources allocated by the state and NGOs.
The current status of the SDS components does not allow ensuring a secured response to the current threats to Ukraine’s national security.
The following unresolved issues remain in the SDS:
1. Inefficiency of the mechanism of preventing and neutralizing current threats to Ukraine’ national security; inefficiency of their prevention;
2. Imperfection of the process of formation, coordination and interaction between the SDS components in solving shared national security tasks;
3. Incomplete process of building an effective national security crisis resource management system;
4. An imperfect system of planning and joint use of troops (forces) and means, their training and support, etc.
The Concept defines security and defense sector reform priorities including:
1. Consolidation of the operational capabilities of the SDS components to ensure a timely and adequate response to crises that threaten national security;
2. Establishing an effective system to command and control the SDS as an integral functional system;
3. Keeping the designated security and defense forces constantly ready to perform the assigned tasks;
4. Improving the SDS planning system, ensuring ra-tional use of state resources.
It is expected to focus the main SDS development efforts on gradual and coordinated build up of security and defense forces operational capabilities and their level of readiness to immediately respond to challenges and threats to Ukraine’s national security, including the following:
1. Improvement of conceptual and doctrinal bases of training and use of SDS troops (forces) and means;
2. Centralization of SDS management in peacetime, in crisis situations that threaten national security, and in special periods; increasing interdepartmental coordination and liaison;
3. Coherent concepts, strategies and programs to re-form and develop the SDS components and the defense-industrial complex;
4. Improvement of the state forecasting and strategic planning system and the system of planning of the use of SDS troops (forces) and means.
The Concept defines the following main directions of achieving the necessary capabilities:
1. Rational distribution of tasks in the SDS, establishment of a security and defense force management system depending on a type of crisis situation (threat) and with due account for manifold risks to national security;
2. Improving the system of planning of use, command, control and interaction of security and defense forces during elimination (neutralization) of current threats;
3. Establishing a unified system of situational centers in the state bodies which are part of the security and defense sector as well as in other central and local authorities; ensuring its effective coordination using the capabilities of the Main Situational Center of Ukraine , ;
4. Improvement of the territorial defense system in order to form an active UAF reserve, introduction of a practical interaction model between territorial defense units and the national armed forces;
5. Establishing a national security and defense monitoring, analysis, forecasting, modeling and decision-making system according to common methods, elaborated with the aid of the Main Situation Center of Ukraine.
Decisions made in the interests of ensuring state defense capabilities are certainly quite responsible and require systematic consideration of many influencing factors. It is possible to make them only after a preliminary study of their impact on the level of military security provided in the state .
Practical implementation of the directions of achieving the necessary SDS capabilities specified in the Concept to ensure the designated level of state military security is complicated by the lack of appropriate scientific and methodological framework and scientific and methodological support.
It should be noted that defense measures as well as state and non-governmental organizations and structures established to implement them are not effective enough under current conditions due to the lack of systematic research and scientifically validated practice of solving military security problems. Besides, as the organizations and structures expand, the effectiveness of their activities deteriorates (due to duplication of certain functions and the struggle for “survival”). At the same time, the money and material resources spent on solving these problems increase significantly.
The results of the undertaken research show that it is almost impossible to achieve the assigned state military security objectives without development and consistent implementation of a single flexible state policy, integration of the SDS forces and means, development and implementation of a unified system of coherent and comprehensively balanced economic, political, informational, and organizational measures adequate to the threats that impend over vital interests of the society and the state.
Undoubtedly, a comprehensive study can be conducted only by means of appropriate models among witch the Conceptual model of managing the integrated countermeasures potential (CMMICP) to military and hybrid threats is a central one. A CMMICP structural scheme is shown on Fig. 1.
A model to manage an integrated potential on countering military threats shall be developed on the basis of system analysis methodology, operations research methods, hierarchy analysis, probability and forecasting theory, expert evaluation and modeling and can be used by senior military and political leadership in situational control centers during planning and implementation of a targeted policy on ensuring the required level of state military security as well as in educational, scientific and research institutions in studies of crisis situations and ways out of them.
The following principles have been defined as the basis to establish the CMMICP to military and hybrid threats:
1. Model openness which enables to expand it (if necessary) with additional modules, use a single SDS database and ensure reliable information protection from various kinds of information threats;
2. Generation of scenarios which allows to simulate probable scenarios of military-political and geopolitical situation in the region;
3. Filtering the proposed measures which enables to substantiate forces and means integration options on the basis of certain criteria, priority of soft power methods in neutralizing threats to the state military security, actual guarantees, and SDS restrictions;
4. Adaptability to the current military-political situation which enables to substantiate measures on ensuring the state military security adequate to the real level, direction, nature and scale of state military threats;
5. Modularity which enables to replace certain partial models (modules) with more accurate and complete as well as to expand a general model.
In this regard, the CMMICP to military and hybrid threats shall ensure :
1. Objective assessment of the military-political situation (MPS) in the region;
2. Assessment of an SDS forces and means potential required (sufficient) to neutralize the identified (predicted) threats;
3. Elaboration of a set of integration options for SDS forces and means that would meet the requirements on neutralization of threats with due account for actual restrictions in the state system of ensuring military security (SSEMS);
4. Elaboration of a priority list of forces and means integration options indicating the magnitude of their integrated potential;
5. Implementation of logical and mathematical procedures for selecting the most rational forces and means integration option which would ensure maintenance of a sufficient level of military security and meet the current restrictions of the SSEMS;
6. Substantiation of a sufficient level of state military security for neutralization of the considered military threats and defining necessary financial and material resources (where necessary);
7. Substantiation of recommendations on adaptation of the military-political model of the state, its foreign, military-economic and military-technical policy to the actual military and political environment in the region for a specific period of time and for the future.
Since practical development of the CMMICP for military and hybrid threats requires a separate study, we will restrict our consideration to its generalized structural scheme (see Fig. 1) with brief comments about the purpose, requirements, tasks solved, inputs and outputs of some modules of the comprehensive model.
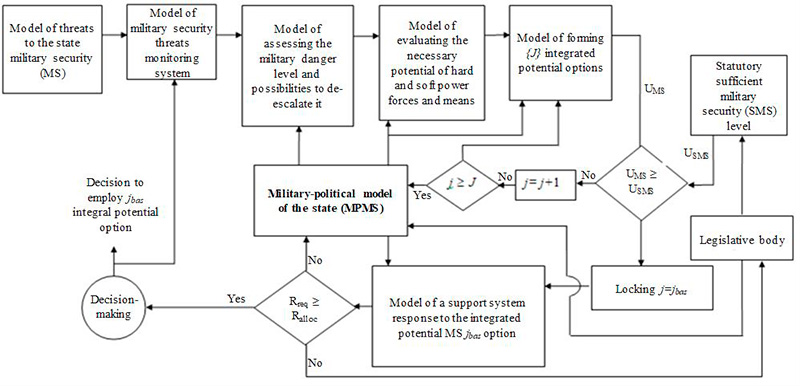
Fig. 1. – Model of managing the integrated potential of countering military and hybrid threats to ensure the assigned level of state military security
Adaptation is carried out through multi-channel feedback which determines the real possibilities of the elaborated options for the integration of forces and means to neutralize the revealed (predicted) threats to ensure the statutory sufficient level of state military security . CMMICP to military and hybrid threats allows to solve both a direct task on calculating the real abilities of the state to ensure military security and a reverse problem on calculating the integrated forces and means potential necessary to ensure the statutory military security level.
Brief description of military and hybrid threats CMMICP main modules is provided below.
Military-political model of the state (MPMS). The MPMS of Ukraine shall be developed on the following bases: the Declaration of State Sovereignty of Ukraine, the Constitution of Ukraine, the Law of Ukraine “On National Security of Ukraine”, the Law of Ukraine “On Principles of Domestic and Foreign Policy”, the National Security Strategy of Ukraine, the Military Doctrine of Ukraine, the Law of Ukraine “On Defense of Ukraine” and other legislative acts on the functioning of the state and ensuring the defense of Ukraine.
The following inputs are usually selected for the MPMS:
1. National state military interests;
2. A scope, direction, and nature of possible use of military force as well as possible strategic partners, allies (obvious and hidden), their possible response to an aggression against Ukraine (a state will choose a hands-off approach, a position of an uninvolved spectator, it will support Ukraine, an aggressor, etc.);
3. Possible amount of assistance or support from neighboring states (blocking approach routes of troops, refusal to provide airspace for air raids, readiness to accept and temporarily accommodate refugees and provide humanitarian aid, willingness and ability to act as a mediator in resolving the conflict, etc.);
4. Possible scales of support for the aggressor (providing corridors for air raids and reconnais-sance, airfields, ports, areas for bases, troops, etc.).
Model of threats to the state military security is a data-base of sometime revealed and predicted military threats each of which shall be described by characteristics of a typical threat passport. “Military threat” means a threat which implementation is accompanied by the use of methods, forces and modern means of contact and non-contact wars or other impacts with the same consequences (destruction, permanent injuries and deaths, functional damage to routine operations and sustainment of the SDS components and critical state infrastructure facilities).
Model of state military security threats monitoring system. The model describes the state statutory-defined procedure for identifying threats to which the system of ensuring military security must respond effectively. This procedure is described in detail . The peculiarities of the monitoring system lie in the fact that it forms a priority list of the revealed threats with sufficient state resources to neutralize them and evaluates effectiveness of the selected option of forces and means integration to counter the threat under consideration.
Model for assessing the military danger level and possibilities to de-escalate it. The model allows to quantify (in the range from 0 to 1) the military danger level per totality of the revealed threats (dangers) both for a certain time interval and for the selected perspective. The model is based on an improved method of hierarchy analysis. The model is described in detail in the monograph . The peculiarity of the model is that it allows to conceptually evaluate SDS ability to de-escalate the revealed level of military danger and to define forces and means that should be used to build an integrated potential for countering the identified threats.
Model of evaluating the necessary potential of hard and soft power forces and means. The model allows to determine SDS capabilities necessary to neutralize a determined (predicted) military danger level. In solving the inverse problem, the model allows to determine forces and means (a potential) necessary to ensure build up of necessary capabilities. These capabilities, in turn, depend on many factors with MPMS being the determining one.
Model of forming integrated potential options. Since the required capabilities can be obtained by different combinations of SDS forces and means available to the state, the model allows not only to form several options [J], but also to rank them according to certain indicators, such as efficiency of the revealed military danged de-escalation, duration, the number of persons involved, etc. Selecting one of forces and means combination options is managing the integrated potential of countering military threats according to the criterion of ensuring the sufficient level of military security if provided with Rreq resources not exceeding the allocated Ralloc resources. The option that match this criterion best is taken as the basic jbas and shall be further implemented by a decision-maker in the SSEMS. Implementation performance is monitored by the threat monitoring system.
If de-escalation of threats is impossible to ensure according to the selected criterion, the model allows to adjust the MPMS, the established sufficient level of military security and search for new opportunities to counter the identified (predicted) threats.
Therefore, the proposed Comprehensive model of managing the integrated counteraction potential enables not only to substantiate the most rational composition of forces and means for de-escalation of the identified (predicted) threats, assess real opportunities to neutralize specific military threats according to the state-approved military security strategies on ensuring military security but also to assess effectiveness of individual components of the SDS forces and means under integration to de-escalate threats to the state. The overviewed conceptual descriptions of partial models include doctrinal provisions that must be used in elaboration of terms of reference for the development of partial computer programs connectable with the Main Situational Control Center software.
Military conflicts of the beginning of the 21st century show a steady trend of comprehensive use of military (force) and non-military (soft power, hybrid) tools. This fundamentally changes the nature of confrontations between conflicting parties. For example, one of the features of the armed conflict in the East Ukraine is that it cannot be resolved by purely power methods and requires broad involvement of soft power entities of the security and defense sector and significant resources.
In a resource-constrained environment it is proposed to ensure Ukraine’s military security through integrating capabilities of the SDS components for timely and effective response to the existing and potential threats. This, in turn, requires development of ways of integrated counter-threat potential formation, comprehensive support and management of its practical implementation based on non-military methods and means, and, if necessary, force support.
Today, the most difficult task is to substantiate necessary military and non-military (hybrid) forces and means and to determine their tasks for guaranteed de-escalation of military threats within the allocated resources.
Analysis of the available substantiation methodology shows that Ukraine mainly employs a method of trials and errors, a method of generating ideas (brainstorming) and methods of expert evaluation (forecasting) that cannot solve the above mentioned problem with sufficient accuracy.
In their previous publications, the authors proposed a method of managing the integrated potential of countering military threats which allows substantiating a rational composition of forces and means and necessary capabilities to de-escalate the identified (predicted) threats to an acceptable level within the resources allocated by both the state and NGOs. However, practical application of this method requires detailed explication of its stages and procedures.
To reduce explanation of symbols let us look only at the information domain. Other domains have similar symbols with different names of the domains in the indexes.
For the information domain:
Рі1 … Ріn – threat indicators and their significance in the information domain;
Р*i1 … Р*in – threat indicators and their admissible residual “weight” after the required level of neutralization “shift” has been achieved;
∆i1 … ∆in – minimum admissible reduction of “weight” (priorities) of the threat indicators according the Saaty scale after the required level of neutralization “shift” has been achieved;
{Pipn} – a set of tasks for an information domain entity on neutralization of the threat indicators to Р*i1 … Р*in levels.
The defined sets of tasks for entities that have formed the integrated response potential represent the required minimum admissible capabilities of these entities and are considered as their partial operational tasks.
Traditionally, a task is considered as accomplished if a sufficient number of executors with capabilities that ensured its implementation have been identified, the resources involved have not exceed the allocated ones, and the losses have not exceed the allowable ones.
Since the proposed method of managing the integrated counteraction potential represents the highest level of systemic use of the SDS entities to neutralize the threat in the military security ensuring system, the target function of the neutralization “shift” should be focused on achieving a synergistic effect as a result of the use of the complex system.
The above mentioned requirement can be practically implemented on the basis of a cognitive approach to the process of preparation and implementation of partial operational tasks based on theory and methods of expert systems, expert-significant intermediate scenarios, analysis of hierarchies and others.
The cognitive approach implies formation of eight expert-significant intermediate scenarios (ESIP) shown in Fig. 2. Scenarios mean expert-chosen relatively independent stages of task definition without which an operational task is impossible to develop.
Let us briefly describe partial tasks solved in each of these expert-significant intermediate scenarios.
ESIP No. 1 – making a decision to neutralize threat Z identified during the monitoring which level exceeded the response threshold of the SSEMS.
The response threshold must be determined in the state’s legal domain. An individual response threshold value shall be statutory defined and added to the appropriate expert system database for each state which is considered as a possible adversary.
ESIP No.2 – selection of entities to form an integrated counteraction potential.
Experts in national and military security employ the brainstorming method using databases of the relevant expert system (ES). It is recommended to select entities that take care of the domains with the most significant signs of the identified threat. Threat passports may be used.
ESIP No. 3 – estimation of the required neutralization “shift” ∆Krnz(Tpr). The required neutralization “shift” is estimated iteratively using M7 computer technology by reducing threat “weight” indicators (priorities) according to the Saaty scale until a value reaches ∆Kns(Tpr) = Kd·∆K(t1), where Kdis the de-escalation coefficient (acquires fixed values:
- if soft power means are used, Kd=1.1;
- if hard power means are used, Kd=1.2).
- If force support is used, Kd=1.15.
Change of military danger level is determined by the equation ∆K(t1) = K(t1)-Kpr as the difference between the current level of military danger (threat) at t1 time and the threshold Kpr (defined in the state legal domain).
(Tpr – t1) – time allotted to neutralize the threat detected at t1 time. It is usually defined at the strategic level and can range from a few months to several years.
ESIP No. 4 – neutralization tasks for each s-th entity and their weight indexes Р*s1 … Р*sn can be determined using a ES knowledge base on threats, an improved hierarchy analysis method, an expert assessment, and M7 computer technology.
Practice has shown that the indicator Р*s can achieve the required “weight” through a set of individual tasks (measures) implemented in the s-th domain. The more such measures are carried out, the faster the desired result is achieved, conversely, resources for their implementation increase (and not always proportionally). This can be blocked in the ESIP No. 8. It is advisable to form a set of such measures for each s-th domain by brainstorming using the ES threats knowledge base. Besides, experts should be prepared to estimate the re-sources needed to implement the proposed options of measures.
ESIP No. 5 – assessment of the current (predicted) neutralization “shift” level ∆Kns(Tpr). The set of tasks (measures) for each domain (the third level of the three-level hierarchical model) determined in the ESIP No. 4 is fed into M7 computer technology. The current (predicted) neutralization “shift” ∆Kns(Tpr) is calculated by means of this technology. Simultaneously, the “weight” (priority) of each domain may be adjusted. This will be taken into account in future during the redistribution of resources, if the need arises. Forecast precision can be improved through the use of ESs and ES-assisted adjusting of factors and conditions that will affect the examined threat level dynamics most significantly.
ESIP No. 6 – the sufficiency of the achieved current (predicted) neutralization “shift” ∆Kns(Tpr) ≥ ∆Knsp(Tpr) is checked. If the condition is met, then the corresponding sets of tasks {Zs} and their “weight” (priority) shall be locked for each s-th sphere in the ESIP No. 4. If this condition is not met, then a new iteration of entity selection in the ESIP No. 2 using the ES shall be carried out, or a new option to reduce threats “weight” (priorities) indicators on the Saaty scale shall be selected in the ESIP No. 3, or a new version of a set of neutralization tasks shall be formed in the ESIP No. 4 (see Fig. 3).
ESIP No. 7 – taking into account the gathered experience and relevant methodological material fed to the relevant ES knowledge base, the resources R∑z required to neutralize the detected threat Z by all entities according to the option locked in the ESIP No. 4. are estimated.
ESIP No. 8 – the required resources R∑z estimated in ESIP No. 7 are matched with the allocated resources R*∑z.
If R∑z ≤ R*∑z is false, then a new iteration is carried out in the ESIP No. 4 or the ESIP No. 3, or the ESIP No. 2 (see Fig. 3).
If R∑z ≤ R*∑z is true, then a draft managerial decision to neutralize the identified threat by the determined composition of entities with the substantiated objectives for each entity shall be submitted for approval to the decision-maker.
Of course, practical implementation of the described expert-significant scenarios requires specific management in the security and defense sector, appropriate information-analytical and resource support. It is advisable to use Main Situational Control Center information resources, technologies and analysts (experts) to implement the proposed method .
Therefore, the developed cognitive approach to defining tasks for military and non-military components involved in the joint neutralization of military threats by integrating their abilities under resource constraints allows to adapt to the level and nature of threats and use military and non-military tools for ensuring military security rationally.
In response to the hybrid aggression against Ukraine characterized by the comprehensive use of military and non-military tools (economic, political, informational and psychological, etc.), the defense concept shall be strategically reviewed. At the same time, development of an effective mechanism to form and implement the state policy on ensuring military security, military-political, administrative and direct military leadership of the defense forces shall be envisaged. The priority is to create an efficient SDS management system.
National defense capabilities are expected to be formed through improved interaction and coordination of actions between government bodies and SDS components with due account for peculiarities of countering the hybrid aggression.
Considering the principles of domestic and foreign policy and the nature of the current national security threats, the main objectives of Ukraine’s short- and medium-term military policy are to create the integrated SDS as the main element of the SSEMS, integrate its components’ capabilities for timely and effective response to actual and potential threats, expand capabilities of the defense forces necessary to achieve military policy objectives with due account for state abilities and resources.
The updated defense concept is based on new methods of defense management according to the criterion of “high efficiency at reasonable costs”.
Acceptable losses are considered mainly in developed democracies where a civil society is the main socio-political force which determines domestic and foreign policy, including in the military sphere, and exercises public control over the government. The civil society considers human life, human rights and security to be the main values. A military solution of foreign policy problems is unacceptable for the civil society if hostilities result in significant losses of material and, especially, human resources. But this allegation applies only to situations that do not threaten the existence of the state. An aggression changes the attitude to losses in order to preserve sovereignty and independence. It is becoming increasingly difficult to use military force in situations that do not threaten the existence of the state as civil society develops. Experiences of military conflicts of various scales show that the level of human resources, especially of the civilian population, is becoming one of the most important factors in restricting the use of excessive military force.
Final remarks
Military threats, especially military threats of a hybrid nature (with signs of hybridity) are formed by many different factors. Military and non-military counteraction forces and means may be integrated on the basis of a large number of forms and methods. This requires to determine a rational composition of forces and means of the security and defense sector components for practical implementation of a determined (selected) de-escalation (neutralization) method of the detected (predicted) threat.
We have proposed the Concept of the comprehensive use of military and non-military forces and means to counter a hybrid aggression (military threats with signs of hybridity) is based on integration of SDS military and non-military forces and means which is a promising area to ensure the sufficient level of military security.
The principles of forming the integrated potential to counter military threats with signs of hybridity and the requirements for comprehensive support and management of its practical implementation have been defined with due account for the priority use of non-military counteraction methods and means and, if necessary, force support.
We have proposed the Conceptual model of managing the integrated countermeasures potential which gives an opportunity not only to substantiate a rational composition of forces and means for de-escalation of the identified (predicted) threats and assess real possibilities for neutralization of specific military threats and threats with signs of “hybridity but also to evaluate the effectiveness of the use of forces and means of individual Ukrainian security and defense sector components integrated to counter the threat.
Methodological approaches to defining tasks for military and non-military components involved in the joint neutralization of threats under limited resources allow to adapt to the threat level and, therefore, rationally use existing military and non-military tools to counter the hybrid aggression.
Literature
- A. Ivashchenko “Evolution of Views on a Modern Hybrid Conflict Strategy and Scenarios of Countering Hybrid Threats”: CMSS NDUU Proceedings. – Kyiv, 2015. – No. 1 (53).
- A. Syrotenko “A Cognitive Approach to Determining Tasks of the Integrated Po-tential Components for de-Escalation of Military Threats in the Military Security System” / A. Syrotenko, V. Bogdanovych, I. Svyda // UAF Air Force Science and Technology. – 2018. – No. 3. – p. 12–18.
- A. Syrotenko “A Concept of the Integrated Use of Military and Non-Military Forces and Means to Ensure a Sufficient Level of State’s Military Security” / A. Syrotenko, V. Bogdanovych, I. Svyda // UAF Air Force Science and Technology. – 2018. – No. 2 (31). – p. 16–29.
- A. Syrotenko “A Method of Adaptive Integrated Capability Management to Counter the Revealed (Predicted) Threat” / A. Syrotenko, V. Bogdanovych, I. Svyda // UAF Air Force Science and Technology. – 2017. – No. 4 (29). – p. 5–10.
- A. Syrotenko “A Methodology of the Comprehensive Use of Military and Non-Military Security and Defense Sector Forces and Means to Counter Current Threats for Military Security of Ukraine”: monograph / A. Syrotenko, V. Bogdano-vych, I. Romanchenko, I. Svyda. – Lviv, 2019.
- A. Syrotenko. “A Methods to Design Necessary Capabilities of the Integrated Potential Components for De-Escalation of Threats at the Executive Level” / A. Syrotenko, V. Bogdanovych, I. Svyda: Proceedings of the UAF Central Research Institute. – Кyiv, 2017. – No. 3 (81). – p. 48–56.
- B. Sovetov “System Modeling”: college textbook / B. Sovetov, S. Yakovlev. – Moscow, 2001.
- Expert Systems: Structure and Classification” : http://www.prorobot. ru/nauka/expert-systems-structure-and-classification.php
- On the Concept of Development of the Security and Defense Sector of Ukraine”: the Decree of the President of Ukraine of March 14, 2016 No. 92/2016. // Official Gazette of Ukraine.
- On the Decision of the National Security and Defense Council of Ukraine of 02.09.2015 “On the New Version of the Military Doctrine of Ukraine”. Decree of the President of Ukraine of 24.09.2015 No. 555/2015 – p. 12.
- On the Decision of the National Security and Defense Council of Ukraine of 12.09.2015 “On the New Version of the Military Doctrine of Ukraine”: the Decree of the President of Ukraine no. 555/2015.On the Decision of the National Security and Defense Council of Ukraine of 02.09.2015 ‘On the New Version of the Military Doctrine of Ukraine’ ”. The De-cree of the President of Ukraine of 24.09.2015 No. 555/2015 // Official Gazette of Ukraine. – 2015. – No. 70 (09.10.2015).
- On the Decision of the National Security and Defense Council of Ukraine of 6.05.2015 ‘On National Security and Defense Strategy’ ”: the Decree of the Presi-dent of Ukraine No. 287/2015. – Official Gazette of Ukraine, 2015.
- On the Decision of the National Security and Defense Council of Ukraine of 4.03.2016 “On the Concept of Development of the Security and Defense Sector of Ukraine”: the Decree of the President of Ukraine No. 92/2016. // Official Ga-zette of Ukraine, 2016.
- On the Decision of the National Security and Defense Council of Ukraine of 14.09.2020 ‘On National Security and Defense Strategy”: the Decree of the President of Ukraine No. 392/2020.’ ” – Official Gazette of Ukraine, 2020.
- T. Saaty “Analytical Planning: The Organization of Systems” ISBN 0-08-032599-8
- V. Bogdanovych “A Comprehensive Model of Managing the Integrated Poten-tial of Countering Military Threats to Ensure the Assigned Level of State Military Security” / V. Bogdanovych, O. Pavlovskyi // UAF Air Force Science and Technology. 2017. – No. 1 (26). – p. 6–11.
- V. Bogdanovych “A Conceptual Model of National Security Information Moni-toring System” / V. Bogdanovych, A. Vysidalko // “Information Protection”. – 2014. – Vol. 16, No.1. – p. 81–88.
- V. Bogdanovych “A Method of Managing the Integrated Potential of Counter-ing Military Threats to Ensure the Assigned Level of State Military Security” / V. Bogdanovych, G. Vorobyov, A. Savostyanov. – Text copyright certificate No. 69125 of 13.12.2016.
- V. Bogdanovych “Methods of Automated Modeling of Expert-Analytical Sce-narios of Detecting and Eliminating Threats to Fulfillment of National Interests” / V. Bogdanovych, A. Vysidalko // UAF Air Force Science and Technology. – 2015. – No. 3 (20). – p. 21–29.
- V. Bogdanovych “Theoretical and Methodological Basis of Ensuring National Security of Ukraine”: monograph: in 7 volumes – Vol. 4. – “State Military Security and Ways to Ensure It” / V. Bogdanovych, I. Svyda, Ye. Skulysh; under general ed. of Ye. Skulysh. – Кyiv, 2012.
- “World Hybrid War: Ukrainian Front”: monograph / under general editorship of V. Gorbulin. – Кyiv, NISS, 2017. – 496 pages.
Citate:
APA 6th Edition
Sirotenko, A. i Semenenko, C.V. (2022). Fundamentals of the Comprehensive Use of Military and Non-Military Forces and Means to Counter the Hybrid Aggression. National security and the future, 23 (2), 19-52. https://doi.org/10.37458/nstf.23.2.1
MLA 8th Edition
Sirotenko, Anatoliy i Colonel Viacheslav Semenenko. "Fundamentals of the Comprehensive Use of Military and Non-Military Forces and Means to Counter the Hybrid Aggression." National security and the future, vol. 23, br. 2, 2022, str. 19-52. https://doi.org/10.37458/nstf.23.2.1 Citirano DD.MM.YYYY.
Chicago 17th Edition
Sirotenko, Anatoliy i Colonel Viacheslav Semenenko. "Fundamentals of the Comprehensive Use of Military and Non-Military Forces and Means to Counter the Hybrid Aggression." National security and the future 23, br. 2 (2022): 19-52. https://doi.org/10.37458/nstf.23.2.1
Harvard
Sirotenko, A., i Semenenko, C.V. (2022). 'Fundamentals of the Comprehensive Use of Military and Non-Military Forces and Means to Counter the Hybrid Aggression', National security and the future, 23(2), str. 19-52. https://doi.org/10.37458/nstf.23.2.1
Vancouver
Sirotenko A, Semenenko CV. Fundamentals of the Comprehensive Use of Military and Non-Military Forces and Means to Counter the Hybrid Aggression. National security and the future [Internet]. 2022 [pristupljeno DD.MM.YYYY.];23(2):19-52. https://doi.org/10.37458/nstf.23.2.1
IEEE
A. Sirotenko i C.V. Semenenko, "Fundamentals of the Comprehensive Use of Military and Non-Military Forces and Means to Counter the Hybrid Aggression", National security and the future, vol.23, br. 2, str. 19-52, 2022. [Online]. https://doi.org/10.37458/nstf.23.2.1
References
- Anatoliy Sirotenko, The Head of the National Defence University of Ukraine named after Ivan Cherniakhovskyi, Kyiv, Ukraine, ORCID https://orcid.org/0000-0002-0266-5706
- *Colonel Viacheslav Semenenko, PhD. The Deputy Head of the Center for Military and Strategic Studies of the National Defence University of Ukraine named after Ivan Cherniakhovskyi, Kyiv, Ukraine, ORCID https://orcid.org/0000-0001-5774-0868
- “On the Decision of the National Security and Defense Council of Ukraine of 02.09.2015 ‘On the New Version of the Military Doctrine of Ukraine’ ”. The De-cree of the President of Ukraine of 24.09.2015 No. 555/2015 // Official Gazette of Ukraine. – 2015. – No. 70 (09.10.2015). – Про рішення Ради національної безпеки і оборони України від 02.09.2015 “Про нову редакцію Воєнної доктрини України”. Указ Президента України від 24.09.2015 № 555 / 2015 // Офіційний вісник України. – 2015. – № 70 (09.10.2015).
Ibid.
- A. Syrotenko “A Methodology of the Comprehensive Use of Military and Non-Military Security and Defense Sector Forces and Means to Counter Current Threats for Military Security of Ukraine”: monograph / A. Syrotenko, V. Bogdano-vych, I. Romanchenko, I. Svyda. – Lviv, 2019. – 268 pages. – Сиротенко А. М. Методологія комплексного використання військових та невійськових сил та засобів сектору безпеки і оборони для протидії сучасним загрозам воєнній безпеці України: монографія / А. М Сиротенко, В. Ю. Богданович, І. С. Романченко, І. Ю. Свида – Львів: НАСВ, 2019. – 268 с.
- On the Decision of the National Security and Defense Council of Ukraine of 12.09.2015 “On the New Version of the Military Doctrine of Ukraine”: the Decree of the President of Ukraine no. 555/2015.
- “On the Concept of Development of the Security and Defense Sector of Ukraine”: the Decree of the President of Ukraine of March 14, 2016 No. 92/2016. // Official Gazette of Ukraine. – p. 45. – Про Концепцію розвитку сектору безпеки і оборони України: Указ Президента України від 14.03.2016 № 92/2016. – К.: АПУ, 2016. – 45 с.
- On the Decision of the National Security and Defense Council of Ukraine of 02.09.2015 “On the New Version of the Military Doctrine of Ukraine”. Decree of the President of Ukraine of 24.09.2015 No. 555/2015 – p. 12.
- A. Ivashchenko “Evolution of Views on a Modern Hybrid Conflict Strategy and Scenarios of Countering Hybrid Threats”: CMSS NDUU Proceedings. – Kyiv, 2015. – No. 1 (53). – p. 18–23. – Іващенко А. М. Еволюція поглядів на стратегію сучасного гібридного конфлікту та сценарії протидії гібридним загрозам: Зб. наук. праць ЦВСД НУОУ. – К. : НУОУ, 2015. – № 1 (53). – С. 18–23.
- “World Hybrid War: Ukrainian Front”: monograph / under general editorship of V. Gorbulin. – Кyiv, NISS, 2017. – 496 pages.
- A. Syrotenko “A Methodology of the Comprehensive Use of Military and Non-Military Security and Defense Sector Forces and Means to Counter Current Threats to Military Security of Ukraine”. – Monograph / A. Syrotenko, V. Bog-danovych, I. Romanchenko, I. Svyda. – Lviv, 2019.
- A. Syrotenko “A Concept of the Integrated Use of Military and Non-Military Forces and Means to Ensure a Sufficient Level of State’s Military Security” / A. Syrotenko, V. Bogdanovych, I. Svyda // UAF Air Force Science and Technology. – 2018. – No. 2 (31). – p. 16–29. – Сиротенко А. М. Концепція комплексного використання військових та невійськових сил і засобів для забезпечення достатнього рівня воєнної безпеки держави /А. М. Сиротенко, В. Ю. Богданович, І. Ю. Свида // Наука і техніка Повітряних Сил ЗС. – 2018. – № 2 (31). – С. 16–29
- A. Syrotenko “A Method of Adaptive Integrated Capability Management to Counter the Revealed (Predicted) Threat” / A. Syrotenko, V. Bogdanovych, I. Svyda // UAF Air Force Science and Technology. – 2017. – No. 4 (29). – p. 5–10.
- Сиротенко А. М. Метод адаптивного управління інтегрованим потенціалом протидії виявленій (прогнозованій) загрозі / А. М. Сиротенко, В. Ю. Богданович, І. Ю. Свида // Наука і техніка Повітряних Сил ЗС України. – 2017. – № 4 (29). – С. 5–10.
- A. Syrotenko “A Cognitive Approach to Determining Tasks of the Integrated Po-tential Components for de-Escalation of Military Threats in the Military Security System” / A. Syrotenko, V. Bogdanovych, I. Svyda // UAF Air Force Science and Technology. – 2018. – No. 3. – p. 12–18. Сиротенко А. М. Когнітивний підхід до визначення завдань складовим інтегрованого потенціалу деескалації загроз воєнного характеру в системі забезпечення воєнної безпеки / А. М. Сиротенко, В. Ю. Богданович, І. Ю. Свида // Наука і техніка Повітряних Сил Збройних Сил України. – 2018. – № 3. – С. 12–18.
- A. Syrotenko “A Concept of the Integrated Use of Military and Non-Military Forces and Means to Ensure a Sufficient Level of State’s Military Security” / A. Syrotenko, V. Bogdanovych, I. Svyda // UAF Air Force Science and Technology. – 2018. – No. 2 (31). – p. 16–29.
- V. Bogdanovych “A Method of Managing the Integrated Potential of Counter-ing Military Threats to Ensure the Assigned Level of State Military Security” / V. Bogdanovych, G. Vorobyov, A. Savostyanov. – Text copyright certificate No. 69125 of 13.12.2016. – Богданович В. Ю. Метод управління інтегрованим потенціалом протидії загрозам воєнного характеру для забезпечення визначеного рівня воєнної безпеки держави / В. Ю. Богданович, Г. П. Воробйов, А. Ф. Савостьянов. – Свідоцтво про реєстрацію авторського права на твір № 69125 від 13.12.2016.
- A. Syrotenko. “A Methods to Design Necessary Capabilities of the Integrated Potential Components for De-Escalation of Threats at the Executive Level” / A. Syrotenko, V. Bogdanovych, I. Svyda: Proceedings of the UAF Central Research Institute. – Кyiv, 2017. – No. 3 (81). – p. 48–56. – Сиротенко А. М. Методика проектування необхідних спроможностей складових інтегрованого потенціалу деескалації загроз на виконавчому рівні / А. М. Сиротенко, В. Ю. Богданович, І. Ю. Свида: Зб. наук. праць ЦНДІ ЗС України. – К., 2017. – № 3 (81). – С. 48–56.
- On the Decision of the National Security and Defense Council of Ukraine of 4.03.2016 “On the Concept of Development of the Security and Defense Sector of Ukraine”: the Decree of the President of Ukraine No. 92/2016. // Official Ga-zette of Ukraine, 2016. – 17 pages. – “Про рішення Ради національної безпеки і оборони України від 4.03.2016 “Про Концепцію розвитку сектору безпеки і оборони України”: Указ Президента України № 92/2016. – К.: АПУ, 2016. – 17 с.
- “On the Decision of the National Security and Defense Council of Ukraine of 6.05.2015 ‘On National Security and Defense Strategy’ ”: the Decree of the Presi-dent of Ukraine No. 287/2015. – Official Gazette of Ukraine, 2015. – 12 pages. – Про рішення Ради національної безпеки і оборони України від 6.05.2015 року “Про Стратегію національної безпеки України”: Указ Президента України № 287/2015. – К.: АПУ, 2015. – 12 с.
- V. Bogdanovych “Methods of Automated Modeling of Expert-Analytical Sce-narios of Detecting and Eliminating Threats to Fulfillment of National Interests” / V. Bogdanovych, A. Vysidalko // UAF Air Force Science and Technology. – 2015. – No. 3 (20). – p. 21–29. – Богданович В.Ю. Методика автоматизованого моделювання експертно-аналітичних сценаріїв виявлення та усунення загроз реалізації національних інтересів / В. Ю. Богданович, А. Л. Висідалко // Наука і техніка Повітряних Сил Збройних Сил України. – 2015. – № 3 (20). – С. 21–29.
- V. Bogdanovych “Theoretical and Methodological Basis of Ensuring National Security of Ukraine”: monograph: in 7 volumes – Vol. 4. – “State Military Security and Ways to Ensure It” / V. Bogdanovych, I. Svyda, Ye. Skulysh; under general ed. of Ye. Skulysh. – Кyiv, 2012. – 464 pages. – Богданович В. Ю. Теоретико-методологічні основи забезпечення національної безпеки України: монографія: у 7 т. – Т. 4. – Воєнна безпека держави і шляхи її забезпечення / В. Ю. Богданович, І. Ю. Свида, Є. Д. Скулиш; за заг. ред. Є. Д. Скулиша. – К.: Наук.-вид. відділ НА СБ України, 2012. – 464 с.
- V. Bogdanovych “A Conceptual Model of National Security Information Moni-toring System” / V. Bogdanovych, A. Vysidalko // “Information Protection”. – 2014. – Vol. 16, No.1. – p. 81–88. – Богданович В. Ю. Концептуальна модель інформаційно-моніторингової системи національної безпеки / В. Ю. Богданович, А. Л. Висідалко // Захист інформації. – 2014. – Том 16, №1. – С. 81–88.
- V. Bogdanovych “Theoretical and Methodological Basis of Ensuring National Security of Ukraine”. – Vol. 4. – 464 pages.
- V. Bogdanovych “A Method of Managing the Integrated Potential of Counte-ring Military Threats to Ensure the Assigned Level of State Military Security” / V. Bogdanovych, G. Vorobyov, A. Savostyanov. – Text copyright certificate No. 69125 of 13.12.2016.
- V. Bogdanovych “Theoretical and Methodological Basis of Ensuring National Security of Ukraine”: monograph: in 7 volumes – Vol. 4. – “State Military Security and Ways to Ensure It” / V. Bogdanovych, I. Svyda, Ye. Skulysh; under general ed. of Ye. Skulysh. – Кyiv, 2012. – 464 pages.
- Ibid.
- V. Bogdanovych “A Method of Managing the Integrated Potential of Counte-ring Military Threats to Ensure the Assigned Level of State Military Security” / V. Bogdanovych, G. Vorobyov, A. Savostyanov. – Text copyright certificate No. 69125 of 13.12.2016.
- T. Saaty “Analytical Planning: The Organization of Systems” ISBN 0-08-032599-8
- B. Sovetov “System Modeling”: college textbook / B. Sovetov, S. Yakovlev. – Moscow, 2001. – 343 pages. – Советов Б. Я. Моделирование систем: Учеб. для вузов / Б. Я. Советов, С. А. Яковлев. – М.: Высшая школа, 2001. – 343 с.
- V. Bogdanovych “A Comprehensive Model of Managing the Integrated Poten-tial of Countering Military Threats to Ensure the Assigned Level of State Military Security” / V. Bogdanovych, O. Pavlovskyi // UAF Air Force Science and Technology. 2017. – No. 1 (26). – p. 6–11. – Богданович В.Ю. Комплексна модель управління інтегрованим потенціалом протидії загрозам воєнного характеру для забезпечення визначеного рівня воєнної безпеки держави / В. Ю. Богданович, О. В. Павловський // Наука і техніка Повітряних Сил Збройних Сил України. – 2017. – № 1 (26). – С. 6–11.
- “Expert Systems: Structure and Classification” [Online resource]: http://www.prorobot. ru/nauka/expert-systems-structure-and-classification.php
- V. Bogdanovych “Theoretical and Methodological Basis of Ensuring National Security of Ukraine”. – Vol. 4. “State Military Security and Ways to Ensure it” – 464 pages.
- V. Bogdanovych “A Method of Managing the Integrated Potential of Counte-ring Military Threats to Ensure the Assigned Level of State Military Security” / V. Bogdanovych, G. Vorobyov, A. Savostyanov. – Text copyright certificate No. 69125 of 13.12.2016.
- “On the Decision of the National Security and Defense Council of Ukraine of 14.09.2020 ‘On Nati-onal Security and Defense Strategy”: the Decree of the President of Ukraine No. 392/2020.’ ” – Official Gazette of Ukraine, 2020. – 12 pages.